Ken's Corner
 It started out as the World Wide Web, and although that term is rarely used, the Internet still uses the terminology that came from that name. We use web browsers to go to websites, sometimes checking out a webpage or two… You get the idea.
It started out as the World Wide Web, and although that term is rarely used, the Internet still uses the terminology that came from that name. We use web browsers to go to websites, sometimes checking out a webpage or two… You get the idea.
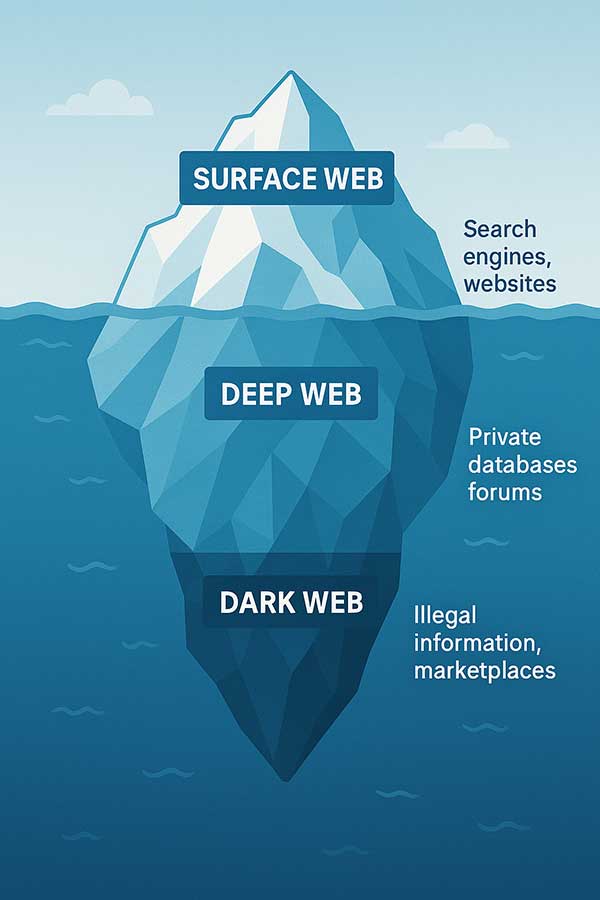
But while it’s called the World Wide Web, that implies there’s only one type of Internet. That’s actually not quite correct. There are three levels of the web, delineated by how you access the data contained in it.
Part one is the Surface Web. Approximately 5 to 10% of the Internet belongs to this category. This is the free stuff; usually no passwords are needed to access these sites although one may be needed to actually use them. The Surface Web is the part you picture when you think of the internet with online shopping, social media and most news/entertainment sites. Depending on the website, security here may be lax to extremely secure, with content running from a small-town ice cream shop to Amazon.
The Deep Web is next, and it’s the largest part of the Internet, occupying 90 to 95% of the world’s total storage. When you access your bank accounts, check out your health records at your local hospital, or send and receive emails, you’re using the Deep Web. Security is stronger here than in the Surface Web because most of it is private information. It’s no coincidence that this is also where hackers do most of their dirty deeds.
Because it is the area where your private data is found, passwords are required for most, if not all, websites on this level. Many of these will also require two-step verification to try to ensure the person accessing your data is actually you.
The final level of the Internet is the smallest and possibly the most dangerous. Making up perhaps .01% of the web storage, The Dark Web is where things happen that no one wants you to know about. While that sounds sinister, it’s not necessarily illegal.
It takes a special web browser to access the Dark Web; Google and Firefox won’t find it. Journalists and others who want private conversations online can do so here because the nature of this part of the Internet makes it very difficult to trace. Because of this, some users will actually shop the Deep Web from here to make the transaction anonymously. This anonymity also lends itself to less-savory activities that are HIGHLY illegal. Web security here is questionable, making this area a tourist location I CANNOT recommend.
- Details
- Written by: CPCC Tech
- Category: Ken's Corner
- Hits: 812
